Anti-malware applications prevent malware from infiltrating and compromising our devices. This is especially important on mobile devices that collect and store large amounts of our personal data. The underlying techniques employed by anti-malware applications include static and dynamic analysis, scrutinising applications both before and during execution to ensure maximum protection. The ongoing struggle between anti-malware application developers and malware authors could be compared to as a perpetual arms race, with each side striving to outsmart the other.
Malware authors have always sought novel methods to evade detection, making use of techniques such as code obfuscation and string encryption to bypass anti-malware defences. However, in recent years, malware authors have adopted a more sophisticated approach, namely that of excluding malicious code from the initial payload and opting to load it from an external source during runtime. This method enables the malware to bypass static analysis, as the actual malicious code would not be present during the initial examination.
Desktop platforms, with their more powerful hardware, could still detect malware, making use of such techniques through heuristics and dynamic analysis. However, mobile devices (including Android smartphones) face limitations in doing so, due to their power constraints and reduced processing capabilities. As a result, these devices are unable to perform dynamic analysis to the same extent as desktop platforms, making them susceptible to more sophisticated attacks.
One such attack vector that takes advantage of this limitation is that of app virtualisation. This technique allows malicious applications to run inside virtual environments created by other applications, significantly enhancing their stealth capabilities. By executing malicious applications within a virtual environment, their visibility is hidden from other applications installed on the device, ensuring that existing detection methods would fail to detect the threat.
The accompanying diagram displays the stealth capabilities of the app virtualisation and the solution being proposed through this project. Firstly, the user would download an application from Google Play that would have app virtualisation capabilities, but does not contain any malicious code. Upon installation, anti-malware applications on the device would scan the application and find no threats. When the user would interact with the virtual container application for the first time, it would set up a virtual environment and obtain a malicious application from an external source, such as an attacker’s server. The virtual container application would then execute the code of the malicious application within the virtual environment, copying its code into volatile memory in the process. Being unaware of this process, any anti-malware applications installed on the device would not respond.
The proposed solution ‒ Virtual Application Scanner ‒ analyses running processes to detect virtualised applications and extracts their code from volatile memory. This code would then be fed back to malware-detection engines to determine whether the virtualised application is malicious.
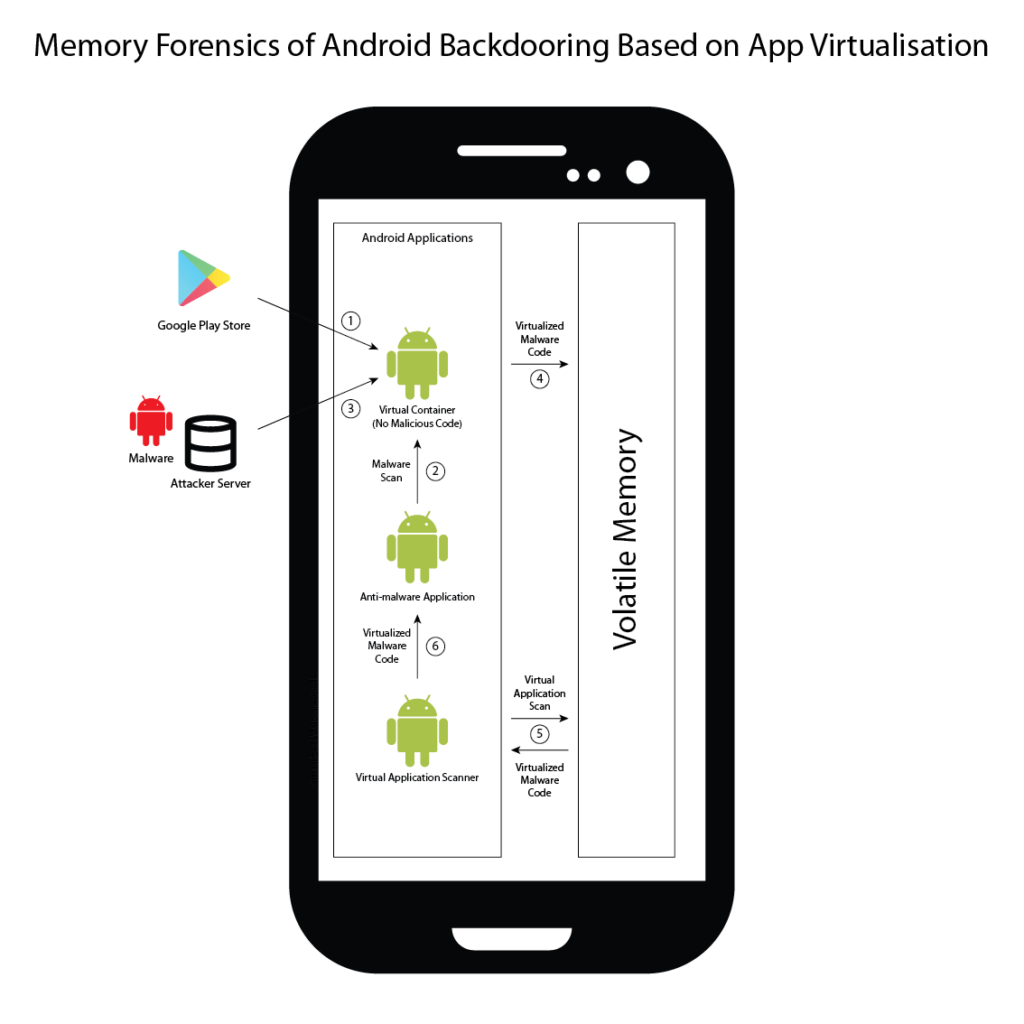
Figure 1. Virtualised application execution and detection process
Student: Enrique Anthony Galea
Supervisor: Dr Mark Vella
