Data leakage is defined as the accidental or unintended distribution of sensitive data to an unauthorised entity [1]. This issue is considered to be one of the largest threats that companies are facing when moving to a cloud infrastructure. New security threats are constantly surfacing targeting data leakages; this is especially so in Software-as-a-Service (SaaS) models [2]. As these services depend on a multitenancy architecture where resources are shared amongst tenants, the issue of data leakage increases in scope. Thus, the Cloud Computing Service Provider (CCSP) has to ensure that data security is in place and that each tenant follows pre-set and accepted security measures. This is the area explored in this research.
Two main approaches have been adopted to carry out this study. First was the design of a SaaS multitenancy database with the necessary configuration requirements (designed for security) for the database server. A middleware was also configured to help serve as both a load balancer and a connection manager. The second approach required the creation of data collection processes that monitor tenant activities, including logon request, query submissions, stored procedure invocations, and delegating data access privileges.
A framework was developed in order to help in the collection and integration of security-related activities and possible identification of threats. Data warehousing techniques were adopted in order to help collate are reconcile data from a variety of data sources e.g. DBMS and middleware logs. As a result, this data warehouse helped to serve as a Log Management system (LMS) – see Figure 1. Also, data mining techniques, such as Rule Mining and Classification algorithms, were implemented. These algorithms use the data available in the Data warehouse (DWH) to help security administrators with the possible identification of data leakage threats in such environments.
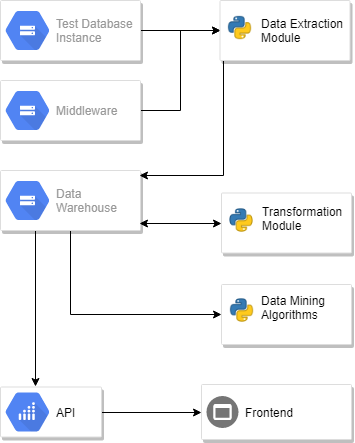
From our experiments, the results show that our suggested framework was effective in gathering data from data sources. Thus, the framework created the possibility of helping administrators at the CCSP and tenants to process activity data and calculate the level of data leakage possibility.
References
[1] C. L. Huth, D. W. Chadwick, W. R. Claycomb, and I. You, “Guest editorial: A brief overview of data leakage and insider threats,” Inf. Syst. Front., vol. 15, no. 1, pp. 1–4, 2013.
[2] D. Ziani and R. Al-Muwayshir, “Improving Privacy and Security in Multi-Tenant Cloud ERP Systems,” Adv. Comput. An Int. J., vol. 8, no. 5, pp. 01–15, 2017.
Student: Julian Calleja
Supervisor: Dr Joseph Vella
Course: B.Sc. (Hons.) Software Development
