The Controller Area Network (CAN) bus protocol is used to network computerised car systems. Security was not a priority when the protocol was designed, as it was initially meant to connect a small number of electronic control unit (ECU) devices in a closed system. Modern cars now have their CAN bus accessible through a diagnostic port and ECUs that communicate wirelessly to outside devices, such as remote keyless entry systems and over-the-air updates to software systems and telematics systems. These systems ‒ combined with the importance of computerised systems in cars, especially in vehicles with self-driving capabilities –would help minimise any security risks that may lead to serious issues spanning from theft of the automobile to injury and possible loss of life. The software-testing method of fuzzing, which is the generation and input of unexpected inputs to a system, has been shown to be a viable attack on devices on the CAN network.
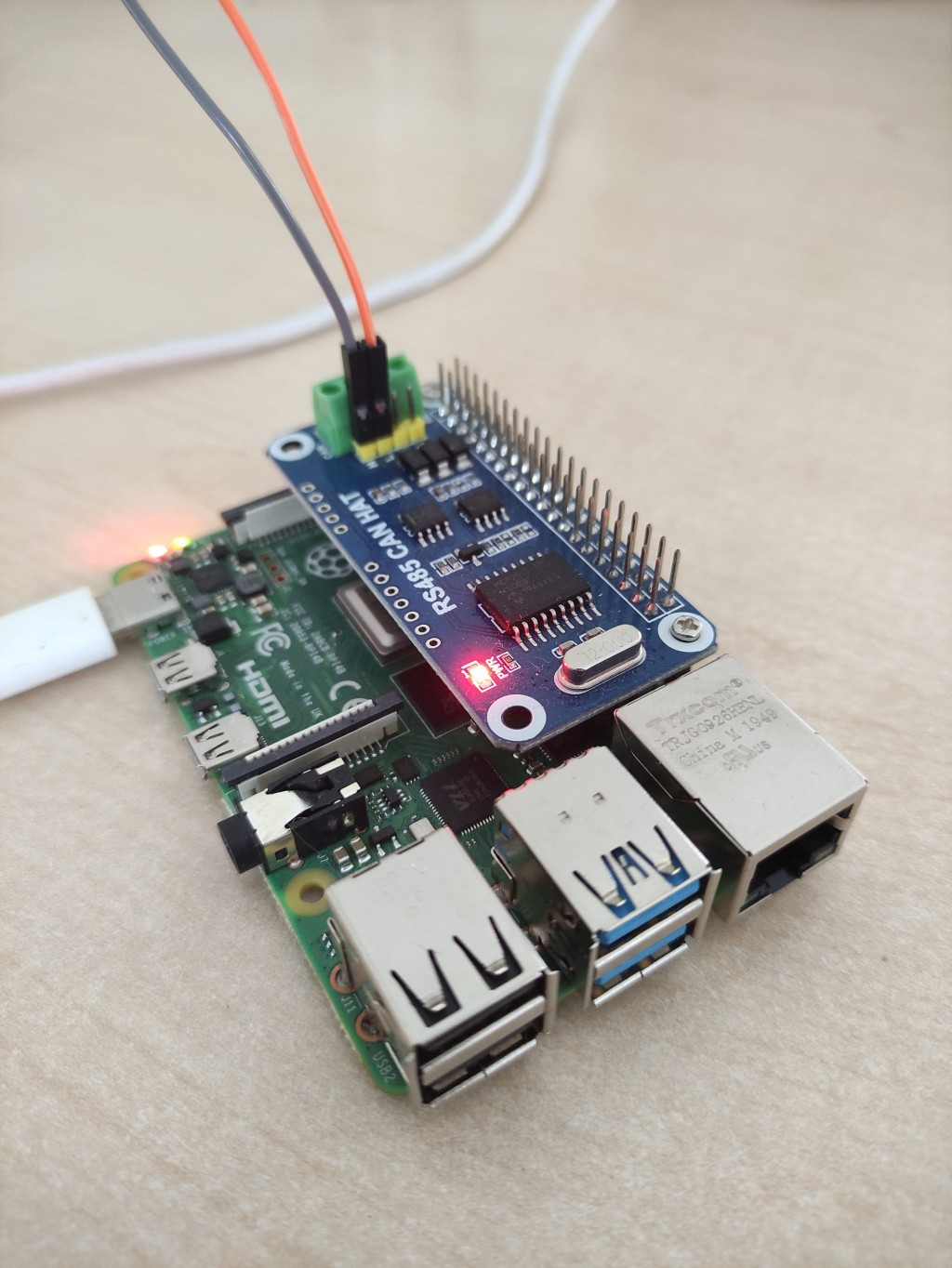
For the purpose of the experiment involving the CAN network, an attack device was developed. This comprised a Raspberry Pi and an MCP2515 module, which allowed the device to communicate with a CAN network. Once connected to the CAN network, the device could monitor all traffic on the network. The resulting data would be used to fuzz messages and send them to the network in order to attack devices on the network. The data could then be viewed, and attacks would be orchestrated through a web interface accessed by connecting to the devices transmitted Wi-Fi network.
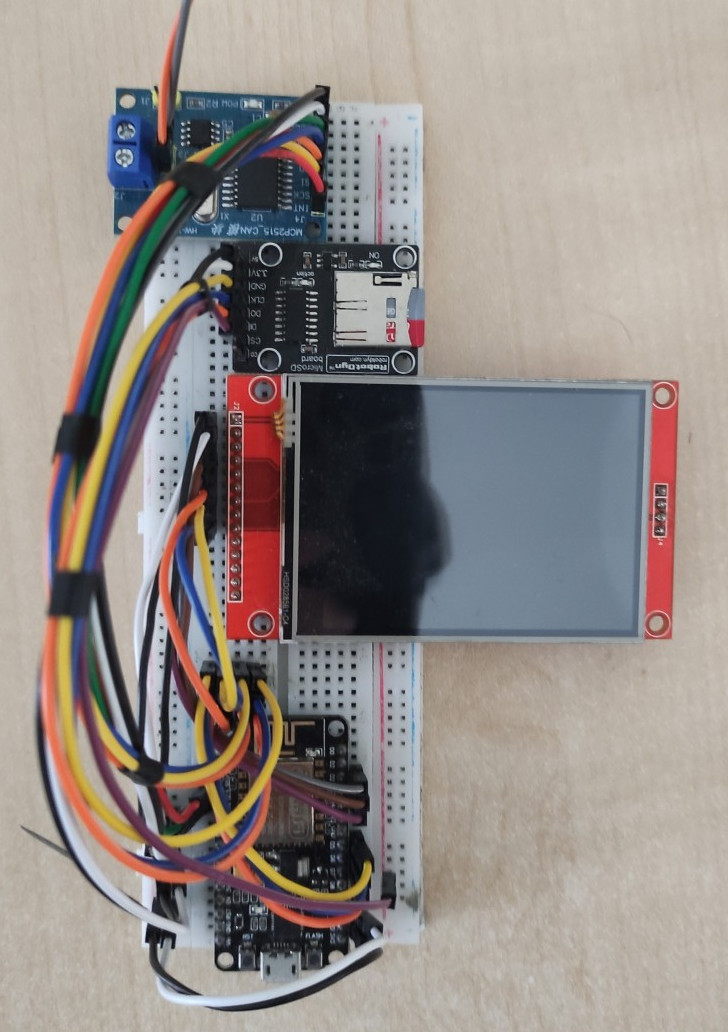
In order to test the attack device itself, a testing device that would emulate the dash system of a car was developed. This device would receive CAN messages and process them with a view to changing instrument values and logging all messages and instrument changes. The testing device consisted of an ESP8266 microcontroller, an ILI9341 LCD screen, an MCP2515 module, and an SD card module.
Course: B.Sc. IT (Hons.) Software Development
Supervisor: Dr Clyde Meli
Co-supervisor: Dr Colin Layfield
