Every action carried out in a system is recorded and logged in memory. These actions, also known as events, could be of various types, such as: opening a file, downloading a file, or accessing a network. Analysing such events is useful for detecting security breaches and computer misuse.
However, events stored in memory are not always analysed, as there are various steps needed to put them into a timeline for easier analysis. Manual checking for any intrusion would be impractical, as it would be very time-consuming to go through all the events, which occur continuously. Hence, automated tools are important and are much needed in this scenario.
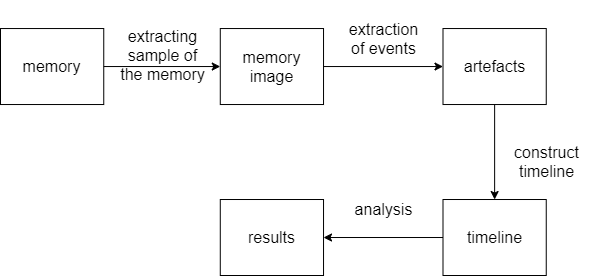
In this project, timelines were checked for any possible intrusions. This process was carried out over a number of stages, as outlined in Figure 1. The first step required is to create a memory image out of the memory. The next step entails extracting events from memory images and constructing the timeline using the Volatility framework. For testing, readily available memory images were used, while timelines without intrusions were created to assess the difference between the two.
The main part involved runtime verification for checking these timelines for any intrusion. The LARVA toolset was used for the analysis, and the timelines were subject to rules to be followed, in the form of transitions. These transitions represent the moves between the states of the timelines. An output file was generated while checking for timelines and if any intrusion is found it would have been reported.
Course: B.Sc. (Hons.) Computing Science
Supervisor: Dr Christian Colombo
Co-supervisor: Dr Mark Vella
