The purpose of this research is to compare the different methods that can be used for still image Steganography, and then create an algorithm that implements one of these methods. Still image
steganography is when basic text is hidden inside a digital still-image by hiding the text inside the pixels of the image. The image can later be decrypted to reveal the message to another user. The application for this software is to be able to send important information discreetly to another user without alerting 3rd parties who may be trying to gather private data through illicit means. The usual method for still image steganography is done by editing the binary value of a number of pixels, depending on the message length, in such a way that the pixel colour only changes very slightly, such that it is not noticeable by the human eye.
Four different steganographic methods were selected, these being the Least significant bit, Pixel value differencing, Discrete Wavelet Transform Technique and Random pixel embedding methods. The reason these 4 methods were chosen in particular was because of their popularity, availability and their security. The results show that none of the methods change the image in a way that can be seen by the human eye, however they all use different methods to achieve this, making it difficult to detect what type of method was used.
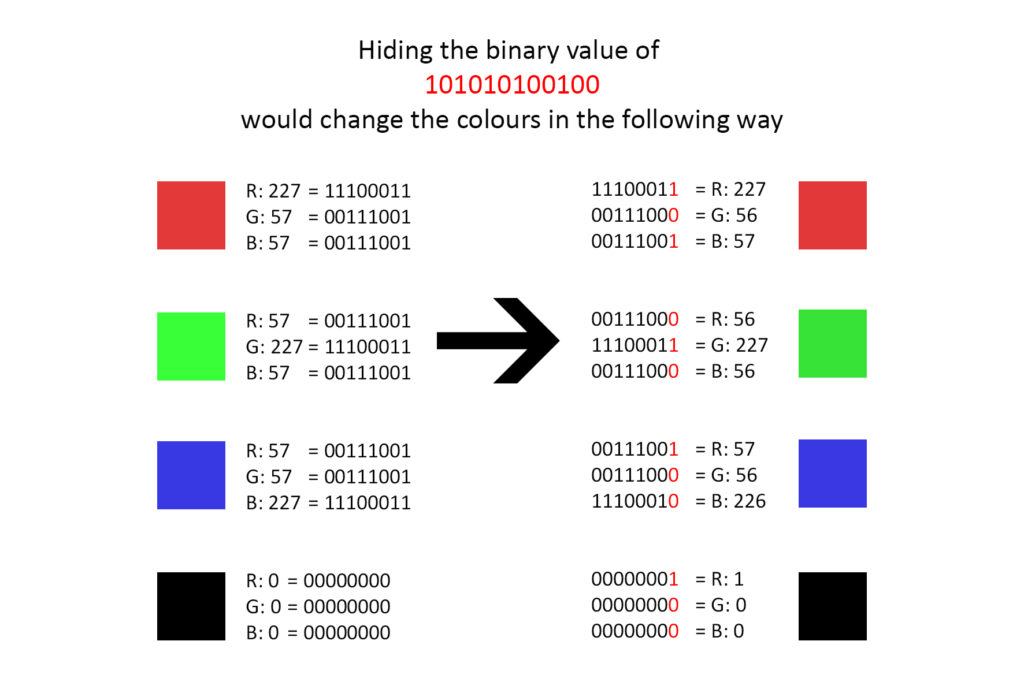
This method works by converting the hidden text and password into a binary string consisting of 1s and 0s. Then it converts every pixel inside the cover image into decimal according to its RGB value and then to binary. Once both of these binary conversions are done, then the algorithm starts to replace the furthest right bit, also called the least significant bit, in the cover image with one binary number from the hidden text and password binary sequence, sequentially for the entire length of the binary string of the hidden text. The reason the furthest right binary number is chosen is because this number changes a single RGB value in a pixel in a very minor way, usually in an increment of 1,-1 or no change at all, thus only leaving a small change that would be very difficult to detect with the human eye and would require specific Steganalysis software. The decryption of the image in order to obtain the data works in a similar way, where the user inputs
the password into the software, it is then converted into binary and compared with the binary password hidden inside the image, if it matches then the rest of the binary string can be decrypted and the hidden text is outputted and shown to the user.
levels relative to their adaptive thresholds and forwarding behaviour.
Student: Andre’ Muscat
Course: B.Sc. IT (Hons.) Software Development
Supervisor: Mr Tony Spiteri Staines
Co-supervisor: Dr Peter Xuereb
