Meltdown and Spectre are hardware vulnerabilities at the microarchitectural level of a central processing unit (CPU), allowing an attacker to manipulate various performance- enhancement techniques in order to extract sensitive data from cache memory [1,2]. The vulnerabilities make direct use of speculative execution, branch prediction and out- of-order execution, whereby the attacker injects malicious code in order to obtain data from the CPU cache memory [1,2]. Software patches for various operating systems and system kernels have been developed and were distributed in order to mitigate the severity of an attack [3]. Since the vulnerabilities in question are relatively new, a watertight preventive solution is yet to be identified. However, these patches have been deployed on Windows and a number of other operating systems have proved to be successful in slowing down the memory-reading process of the attack [4]. Gauging the performance impact of these patches entails the utilisation of benchmarking tools. Therefore, a number of benchmarking tools were tested in order to establish which was the most relevant for this study. The benchmarks were filtered out of the study according to their configuration capabilities and their relevance in terms of any changes that the patches implemented, mainly: out-of-order execution, branch prediction and speculative execution [1,2]. This criterion was adopted primarily because the changes that were introduced related directly to these functionalities.
It was concluded that the benchmarking tool 7-Bench5 would be the most suitable, since it makes direct use of the aforementioned operations, in particular branch prediction and out-of-order execution. The benchmarking tool was implemented on a wide variety of modern- generation processors and system frameworks, such as virtual machines and cloud-based systems, in order to analyse the impact that such patches have caused across various platforms. The benchmarking tool was executed on the systems in various scenarios, covering benchmarks with all the patches enabled and disabled, and for each patch individually.
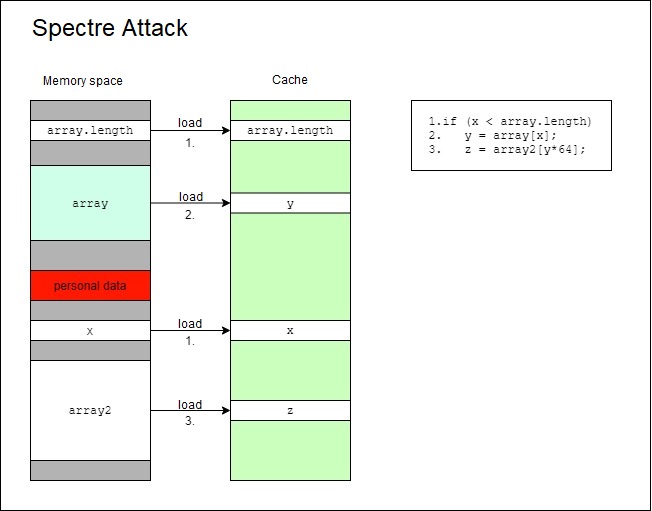
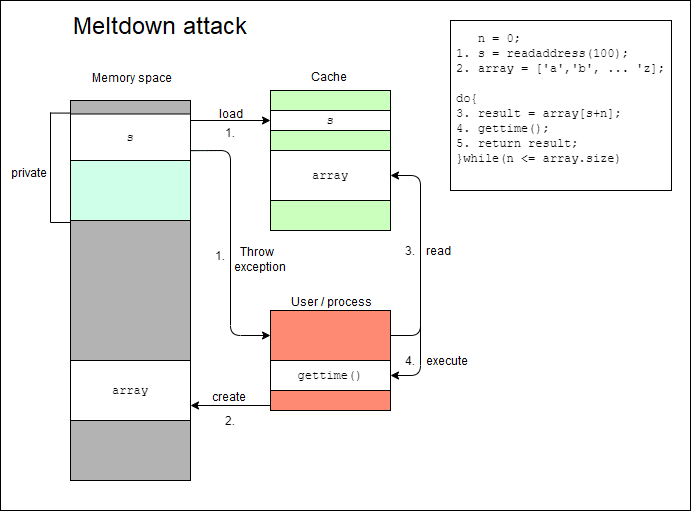
The results obtained from the said benchmarks were then analysed in order to determine any resulting performance-degradation impacts by comparing the results with the default scenario, where all the patches available were enabled. Finally statistical analysis was used to test the hypothesis set for this study.
References/Bibliography:
[1] M. Lipp et al., ‘Meltdown: Reading Kernel Memory from User Space’, in 27th USENIX Security Symposium (USENIX Security 18), 2018
[2] P. Kocher et al., ‘Spectre Attacks: Exploiting Speculative Execution’, in 40th IEEE Symposium on Security and Privacy (S&P’19), 2019.
[3] https://www.csoonline.com/article/3293015/patching-windows-for-spectre-and-meltdown-a- complete-guide.html
[4] O. Alhubaiti and E. M. El-Alfy, “Impact of Spectre/Meltdown Kernel Patches on Crypto-Algorithms on Windows Platforms,” 2019 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakhier, Bahrain, 2019, pp. 1-6, doi: 10.1109/3ICT.2019.8910282.
[5] https://www.7-cpu.com/utils.html
Student: Kevin Agius
Course: B.Sc. IT (Hons.) Software Development
Supervisor: Dr. Clyde Meli
