In their ongoing pursuit of developing malware, a common technique used by malware authors is process injection, through which malicious code is injected into benign processes with escalated privileges. In the past, signature-based detection was generally considered to be sufficient for malware detection. However, with the advent of polymorphism [1] ‒ which became one of the most prevalent detection-evasion techniques ‒ anti-virus signatures were no longer effective, due to the malware’s ability to change its appearance virtually at will.
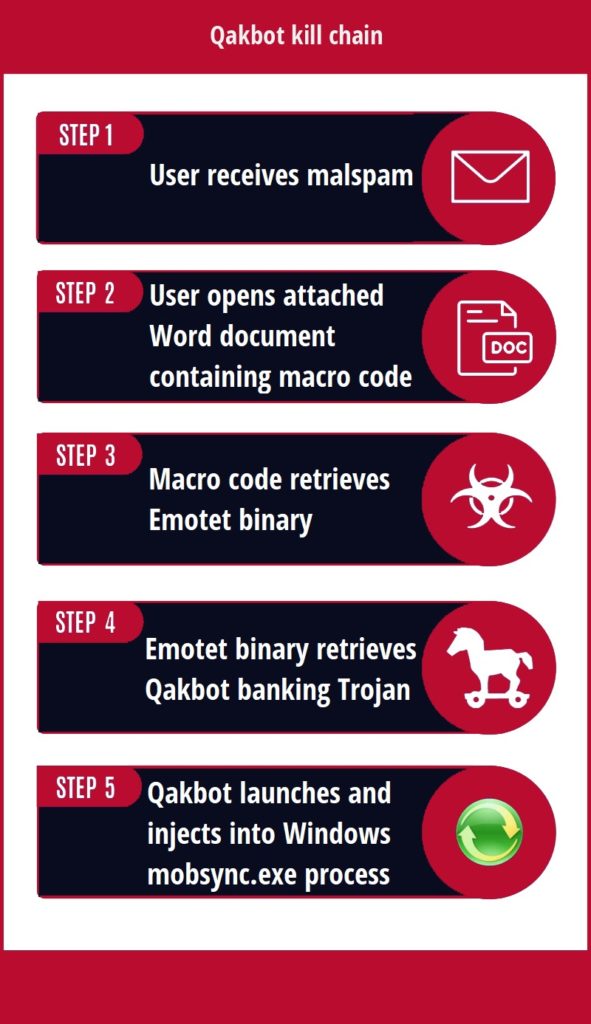
Qakbot [2] is a prime example of malware that, notwithstanding the numerous signatures [3,4] written over the years, continued to evolve and evade detection [5]. Consequently, the detection of the Qakbot sample would be delayed [6], necessitating the use of digital investigation tools for incident response. This malware has evolved and managed to blend into regular Windows processes (see Figure 1), emphasising the importance of memory forensics in identifying the exact workings of Qakbot [2] and the necessity of reconstructing the timeline of events occurring after the malware infection. A prominent obstacle to the analysis of the Qakbot malware is that it includes a packing layer [7] that compresses parts of the malware to avoid detection, and thus hindering analysis.
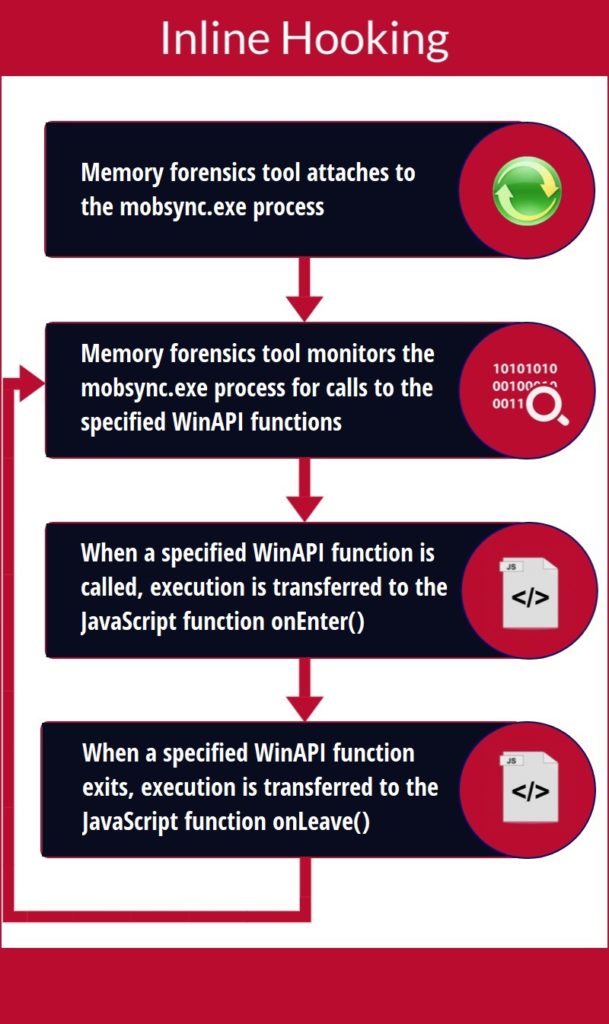
In this study, reverse software engineering (RSE) [8] and dynamic binary instrumentation (DBI) [9] techniques were used to produce forensic tools to assist incident responders in identifying precisely the processes being created and potentially injected. The first tool that was developed was based on state-of-the-art system logs and memory forensics. This would provide a very reliable indication, but not watertight proof, that the benign process being injected is indeed mobsync.exe. The second tool is very similar to the first, with the addition of volatility filters that attempt to detect the newly discovered information from advanced analysis. The third and final tool that was developed is a custom tool based on DBI (see Figure 2) which, through partial but timely memory dumps, could obtain the necessary infection evidence. The complete mobsync.exe misuse picture comes at the expense of computer memory and storage overheads.
Figure 2. Dynamic Binary Instrumentation Through Inline Hooking
References/Bibliography:
[1] Lord, N. (2018, September 11). What is Polymorphic Malware? A Definition and Best Practices for Defending Against Polymorphic Malware. Retrieved from https://digitalguardian.com/ blog/what-polymorphic-malware-definition-and-best-practices- defending- against-polymorphic-malware
[2] Falliere, N. (2009). W32.Qakbot in Detail. Retrieved from https://web.archive.org/web/20191010084219/http://www. symantec.com/ content/en/us/enterprise/media/security_ response/whitepapers/w32_qakbot_in_detail.pdf
[3] Barabosch, T. (2017, April 21). qakbot.yara. Retrieved from https://github.com/tbarabosch/quincy-complementary-material/ blob/ master/yara/qakbot.yara
[4] Yara Rules. (2019, July 5). Retrieved from https://malpedia.caad.fkie.fraunhofer.de/details/win.qakbot
[5] Benge, A. & Randolph, N. (2019, May 2). Qakbot levels up with new obfuscation techniques. Retrieved from https://blog. talosintelligence.com/2019/05/qakbot-levels-up-with-new- obfuscation.html
[6] 2018-12-14 – Emotet infection with Qakbot. (2018, December 14). Retrieved from https://www.malware-traffic-analysis. net/2018/12/14/index.html
[7] K2 Intelligence. (2017, April 28). Qakbot: Insight into a Persistent, Polymorphic Malware from the Cyber Defense Team at K2 Intelligence. https://www.jdsupra.com/legalnews/qakbot- insight-into-a-persistent-26871/
[8] Introduction to Software Engineering/Reengineering/Reverse Engineering. (n.d.). Retrieved from https://en.wikibooks.org/wiki/ Introduction_to_Software_ Engineering/Reengineering/Reverse_Engineering
[9] Dynamic Binary Instrumentation. (2007). Retrieved from http://uninformed.org/index.cgi?v=7&a=1&p=3
Student: Steve Borg
Course: B.Sc. IT (Hons.) Software Development
Supervisor: Dr. Mark Joseph Vella